Difference between revisions of "The Future of Privacy in 2015"
m |
m |
||
| (85 intermediate revisions by 5 users not shown) | |||
| Line 2: | Line 2: | ||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Introduction</h1> | <h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Introduction</h1> | ||
<div style="text-align: justify; padding-bottom: 10px;">Privacy in itself is a term often used, but never defined clearly. Psychologists, philosophers, scientists and linguists debate over the meaning. Aside from the ambiguity of the meaning of the word, there is much changing in the field of privacy. The question is: Where will privacy be, as an issue, in 2015? To answer this question extensive research has to be done first into different aspects of privacy: What is done against it, what is done to create privacy invasion, what rules are set, how do different people value privacy, etc. Upon answering these questions, scenarios will be created for the world of privacy in the future. | <div style="text-align: justify; padding-bottom: 10px;">Privacy in itself is a term often used, but never defined clearly. Psychologists, philosophers, scientists and linguists debate over the meaning. Aside from the ambiguity of the meaning of the word, there is much changing in the field of privacy. The question is: Where will privacy be, as an issue, in 2015? To answer this question extensive research has to be done first into different aspects of privacy: What is done against it, what is done to create privacy invasion, what rules are set, how do different people value privacy, etc. Upon answering these questions, scenarios will be created for the world of privacy in the future. | ||
<br /> | |||
</div> | </div> | ||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Research</h1> | <h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Feedback</h1><p> | ||
[[Questions regarding the Future of Privacy]]<br /> | After we presented the scenarios below, we received the following feedback. | ||
[http://scenariothinking.org/wiki/index.php/Sources_regarding_the_Future_of_Privacy Sources of information and interesting links]<br /> | <br /> | ||
[http://video.google.com/videoplay?docid=4729189253956590972&q=power+of+nightmares+3 '''VIDEO''': The Power of Nightmares 3 of 3] - In this eye-opening video, a more realistic view is given of terrorism, and the 'War Against Terror' | * ''name the scenarios'' | ||
* ''tautology if you have an axes describe the topic<br /> | |||
potential axes could be the idea of distributed system of identity, vs. centralised system of identity'' | |||
* work in a dominance to a certain set of technologies, rather than making it total | |||
* ''remove the earning more and working less, not plausible'' | |||
* ''address actual amount of data'' | |||
* what about interconnected data | |||
* ''what is the rule of law in these scenarios''</p> | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Research & Information</h1> | |||
* [[Questions regarding the Future of Privacy]]<br /> | |||
* [http://scenariothinking.org/wiki/index.php/Sources_regarding_the_Future_of_Privacy Sources of information and interesting links]<br /> | |||
* [http://video.google.com/videoplay?docid=4729189253956590972&q=power+of+nightmares+3 '''GOOGLE VIDEO''': The Power of Nightmares 3 of 3] - In this eye-opening video, a more realistic view is given of terrorism, and the 'War Against Terror' | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Driving Forces</h1> | <h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Driving Forces</h1> | ||
Driving forces categorized by [http://www.valuebasedmanagement.net/methods_PEST_analysis.html PEST] factors method. <br /> | Driving forces categorized by [http://www.valuebasedmanagement.net/methods_PEST_analysis.html PEST] factors method. <br /> | ||
Every driving force in the categories below are built up out of predetermined constituents: ''Description, Enablers, Inhibitors, Paradigms, Experts,'' and '' | Every driving force in the categories below are built up out of predetermined constituents: ''Description, Enablers, Inhibitors, Paradigms, Experts, Timing'', and ''Web Resources'' | ||
<h2 style="background-color: #F5F9FA; border-left | <h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Political</h2> | ||
'''New''' | '''New''' | ||
# [[Perception_of_Terror]] - The perception of terror is slowly changing | |||
# [[immigration]] - Growing immigration in the western countries | # [[immigration]] - Growing immigration in the western countries | ||
# [[European_Union]] - Growing European Union | # [[European_Union]] - Growing European Union | ||
| Line 24: | Line 38: | ||
# [[Control of the Internet]] - Control over the internet | # [[Control of the Internet]] - Control over the internet | ||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border- | <h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Economic</h2> | ||
'''New''' | '''New''' | ||
# [[Electrical component costs]] - Cheaper integration of cameras or audio-recording equipment<br /> | # [[Electrical component costs]] - Cheaper integration of cameras or audio-recording equipment<br /> | ||
| Line 35: | Line 49: | ||
# [[Energy crisis in Asia]] | # [[Energy crisis in Asia]] | ||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border- | <h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Social</h2> | ||
'''New''' | '''New''' | ||
# [[Globalization]] - improvement on existing Driving Force | # [[Globalization]] - improvement on existing Driving Force | ||
| Line 50: | Line 64: | ||
# [[Urbanization and Social Status]] <br /> | # [[Urbanization and Social Status]] <br /> | ||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border- | <h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Technological</h2> | ||
'''New''' | '''New''' | ||
# [[Data Warehousing]] | # [[Data Warehousing]] | ||
| Line 68: | Line 82: | ||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Diagrams</h1> | <h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Diagrams</h1> | ||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border- | <h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Systems diagram</h2> | ||
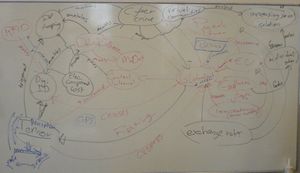
===Version 1 - 'Brainstorm' edition=== | ===Version 1 - 'Brainstorm' edition=== | ||
In order to start creating a system diagram, the initial, unmodified driving forces were mapped into a 'brainstorm' system diagram. | In order to start creating a system diagram, the initial, unmodified driving forces were mapped into a 'brainstorm' system diagram. | ||
| Line 75: | Line 89: | ||
'''A)''' Globalization should be split up into more defined driving forces<br /> | '''A)''' Globalization should be split up into more defined driving forces<br /> | ||
'''B)''' Globalization and terrorism are on their own very complex topics at this moment, so they require further in-depth research.<br /> | '''B)''' Globalization and terrorism are on their own very complex topics at this moment, so they require further in-depth research.<br /> | ||
'''C)''' Politic, as found as a driving force, is a category. An actual driving force must be specified from this category.<br /> | |||
Terrorism is something most people associative with the rhetoric as presented by the media, however, there is a difference between the reality and the rhetoric. Our task is to find our the difference so we can correctly find some distilled driving forces. | Terrorism is something most people associative with the rhetoric as presented by the media, however, there is a difference between the reality and the rhetoric. Our task is to find our the difference so we can correctly find some distilled driving forces. | ||
<br /> | <br /> | ||
This version will be improved upon once the extra research has been completed and posted as version 2 below. | This version will be improved upon once the extra research has been completed and posted as version 2 below. | ||
<br><br><br> | <br> | ||
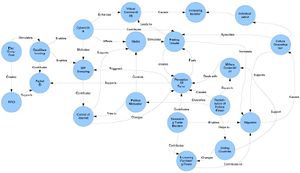
===Version | |||
''This version of the | ===Version 2 - Completing === | ||
[[Image:System_Diagram.JPG|thumb|left|'''Version 2 of the brainstormed system diagram''']] | |||
This is the second version of out system diagram. The two centered spots we had in the first diagram are now worked out. We changed 'terror' in 'perception of terror' and 'Globalization' is worked out in several new parts. A lot of aspects still missing though.<br /> | |||
Planning for version 3:<br /> | |||
*Clear inhibitor/enabler distinction | |||
*Improved edge naming | |||
*More driving forces | |||
*Logic fixes | |||
<br> | |||
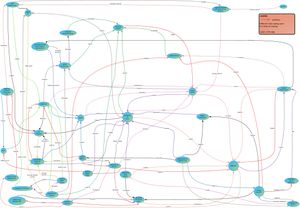
===Version 3 - Semi-Final=== | |||
[[Image:FutOfPriv-SystemDia_final.JPG|thumb|left|'''Version 3, and the semi-final systems diagram''']] | |||
This is the semi-final version of the systems diagram. Messy, but complete. However there is always room for more loops and additions, but through feedback loops and other control mechanisms we managed to keep it to a minimum. | |||
<br /> | |||
<br /> | |||
<br /> | |||
<br /> | |||
<br > | |||
<br /> | |||
<br /> | |||
<br /> | |||
<br /> | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Defining the scenarios</h1> | |||
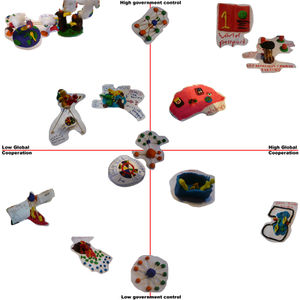
[[Image:Scenario-axis-claydough.jpg|thumb|left|]] To define our scenarios we used an experimental technique. We created two possible futures during a clay dough session in which scenarios were visualized. The first possible future concerned future events relating to the driving forces that each group member had worked on. For the second future every group member pictured a news paper article in the future concerning privacy on a slow newsday. | |||
[http://scenariothinking.org/wiki/index.php/Image:Scenario-future1.jpg Image of first future] | |||
[http://scenariothinking.org/wiki/index.php/Image:Scenario-future2.jpg Image of second future] | |||
With these two futures we were able to find some common denominators for all events that were depicted. Each event contained a level of global cooperation and a certain level of government control. This is how we established the X and Y-axis that we used for our scenarios. In the picture on the left all the events are placed within these axis. These events are not necessarily used in the scenarios, but merely functioned as guidelines to establish the main drivers of our actual scenarios. | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenarios</h1> | <h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenarios</h1> | ||
<h2 style="background-color: #EFF6F8; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenario Axes</h2> | |||
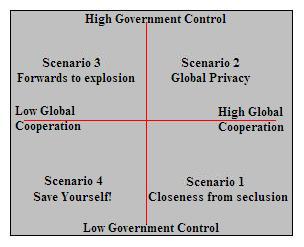
[[Image: Future_of_privacy_axes.JPG]] | |||
<h2 style="background-color: #EFF6F8; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenario 1: Closeness from seclusion</h2> | |||
<p> | |||
In 2015, everybody is aware of their own status of privacy, and in full control of it. Laws are in place to protect personal information, allowing information only to be used for the exact purposes it was given out for by the owner. Technology has made it possible to transmit and store information in utter privacy, while new-age complex encryption technologies make this possible. People carry their private information with them in transmittable format at all times. Back in 2007 this was already a non-issue seeing as personal portable data storage devices the size of cigarette lighters and smaller already had a capacity of up to four gigabyte. This amount is more than sufficient to store any person-critical information of any format. Also, physical privacy is improved with devices to scramble electronic signals, being able to create Faraday-like cages around personal areas, this was still a problem in 2007 as there was no such thing as a 100% secure personal storage device. | |||
People feel safer as they know exactly what is known of them by whom, when and where.<br /> | |||
Laws are in place to protect people’s privacy unconditionally, also when moving around, which makes migration between different countries a political nightmare, but due to high global cooperation, this problem was solved as governments worked together to agree on wide-spread privacy laws. However, this poses a problem for the rule of law concerning the storage and use of private information. Giving the people the power over their own information reduces the control a government has over the information. The government can then no longer decide how to use the information. The question is then whether there should be special laws excluding certain occasions, controlled by the government, in which the privacy of the people can be abused.</p> | |||
<p> | |||
Around 2005, personalized advertising was thought to be the future. However, with the new privacy laws and people being critical of who gets access to their data, there is no room for personalized advertising. Advertising stagnates. Since technology has made it near impossible to create online advertising, it is a marketing-man’s nightmare. Economic recession follows shortly for a brief period of time as retailers recover and fall back to more primitive methods of marketing. | |||
The vast growing network of virtual communities is inhibited as no data is communicated and the communities are very impersonal. | |||
People are weary of spreading their personal data and hold onto it very well, leading to social interruption, individualization and isolation.</p> | |||
<p> | |||
As data is not kept, or may not be kept without permission, bureaucratic practices are rising. Constantly having to ask permission for everything and from multiple people increases the amount of communication needed per transaction. Thankfully, technological advancements in communication compensate for this reasonably well. The crucial data per person, perhaps including electronically stored biometrics and photographs, does not, and seemingly, will not exceed the exorbitant amount of 512 megabytes. Of this amount, only some of it is relevant to be copied at designated places. At an airport, they might only be interested in one or two pictures, your social security number, name, height, age, and a few others figures. This would total a much smaller amount than the total stored. Transferring approximately 50 megabytes takes less than a quarter of a second. This poses no problem for mass reading of multiple data from multiple people uses multiple media (wireless, wired, scanners).</p> | |||
<p> | |||
Perception of terror has been limited to more reality and less speculation and media-induced ideology. The hype has been suppressed. How could anybody possible still attack me? They don't know anything about me! <br /> | |||
I love how we've gotten so close.....what's your name again?</p> | |||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenario 2: Global Privacy</h2> | |||
<p> | |||
The year is 2015. As the world was changing fast for the last couple years, privacy eroded slowly. Governments are connecting throughout the entire world, not only the EU is rapidly growing, also there are incentives to connect the EU to the US. Cultures came together and cultural differences slowly changed and overlapped which leaded to individualism. The amount of immigration was slowly taken back just because of the globalization and uniting countries. Extremism and crime was slowly taken down by the integration. People got very happy as they were feeling very safe in a world with less terror and crime. | |||
</p> | |||
<p> | |||
New technologies came available which made everyone and everything traceable. The amount of privacy was therefore lowering but almost nobody was caring as long as they were safer. All the uniting countries agreed on one global data warehouse and a world identity. Due to this traceability almost all (cyber)crimes were solved and SPAM was not possible anymore. The use of internet got a more important role in the world society. Everyone has a virtual identity which is not only used for playing games but also virtual businesses are rapidly growing. Internet made it possible to store exchanged information. Phone calls were only made via VOIP. Other technological evolutions were used to integrate people among various ‘countries’. Digitalizing the world took care of disappearing brick and mortar shops. The internet was now the way to do your shopping and as it evolved the amount of literacy found in a ‘normal’ book format was brought back to only a few. The digital literacy period has been entered where every information and book you wanted to read was for free available. All these information could more easily be found as you credentials and information searches were profiled on the internet with public access by companies. | |||
</p> | |||
<p> | |||
The political power was equally divided, which got some resistance from the largest former countries in the world. The world got into economic recession but was slowly recovering as the politicians agreed on changing laws and making things more globally. | |||
</p> | |||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenario 3: Forwards to explosion</h2> | |||
<p> | |||
This 3rd scenario is based on the future with high government control, which leads to low level of privacy in the world where global cooperation wasn’t really developing and stayed in almost the same level as it is now. | |||
</p> | |||
<p> | |||
Today with growing economy level in so called “developing” countries the amount of emigrates will slowly decrease. This will lead to several changes in different sectors. First of all, with increase of living standards, people will be more able to use communication technologies and media. The result will be huge invasion into personal privacy. Interruption of privacy at that moment will be not only because people are able to do that, and they are curious in others personal life, but also because of today politics there will be intervention. In other words there is a growing protection from terrorism: so called “world protectors” and “anti-terrorists” are searching all over the world the dangerous information. This is done without yours personal permission and there is nowadays almost no protection for that. Besides that, the new safety video cameras are working with the same idea: intervention into yours privacy without yours admission to protect from possible damage or danger. Additionally, politics very often not only misinterpret but also misuse information. To conclude, privacy invasion is grown to a new level: from leisure to protection from possible danger. | |||
</p> | |||
<p> | |||
The other point necessary to mention is, that people nowadays don’t really care how much and how personal/ important information they put for example on the internet. As mentioned before, politics often misuse the information, but there are many other segments where unsafe information could be used. Of course, the information can be used not only for damaging, but some people can gain advantage of it, like personalized advertisement or helping with tax filling (for example DigiD in the Netherlands). | |||
</p> | |||
<p> | |||
With growing software and hardware and other many technologies the level of protection will be not enough to secure it. Constant hacks into sensitive databases will lead to decrease of retained information. Of course with possible transparency the level of interventions could decrease, and everybody in “illegal” privacy activities will be caught. Unfortunately the cyber-crime (phishing, hacking, scripting, malicious code and spamming) is still growing. The data can be 99% secure, but the possible brake into especially important information can cause really big damages. | |||
</p> | |||
<p> | |||
Adding to this point, people, who are willing to save time on online activities: web-shopping, banking, phoning, etc. need to give up a lot of necessary (or not) personal data. This leads to riot of privacy issues: people who are involved directly and understand the importance of shared information aren’t willing to distribute it. Within this scenario they will suffer the most. Others are not interested yet, but they will get the grunt of privacy issues too. This should lead to new laws for protection of privacy, but the basic damage is already done. | |||
</p> | |||
<p> | |||
To conclude, within this scenario, in around 2015 while regular people will have advantages, unfortunatelly they will suffer the most. Thought the criminals (probably politics too) will have huge advantages of it.</p> | |||
<h2 style="background-color: #F5F9FA; border-left:1px solid #AAAAAA;border-bottom:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Scenario 4: Save yourself!</h2> | |||
<p> | |||
When looking at the world now, you might be optimistic about future cooperation, but actually the signs undermining this vision are already sounding their warning bells very loud and clearly. The efforts by the WTO to open up trade borders are actually seen by 3rd world countries as a way of economic colonization. This has for instance triggered Bolivia, Cuba and Venezuela to form an ‘axis of good’ to oppose the capitalist US which they see as an ‘axis of evil’. Cuba under leadership of Evo Morales has also nationalized the natural gas industry, turning the wheel on open markets backwards. This economic rift between the first world and the third world is also visible in the military interventions and ‘peace keeping’ missions send out by first world countries. Also between the rich countries there is more friction then one might suspect, with the US pushing to invade privacy more in order to prevent terrorist attacks and even forcing instances in Europe to give up data which should be protected by European privacy laws. Going even a step further Bush has signed a law that authorizes the use of military force to liberate any American or citizen of a U.S.-allied country being held by the [International Criminal] court, which is located in The Hague.</p> | |||
<p> | |||
All this anonymity combined with a growing awareness that governments and private institutions might know too much about the people helps to fuel a feeling of distrust and of not being safe. Some governments like the UK try to fight this by invading it’s civilians privacy even more, for instance, their latest effort was to install talking security camera’s, which enabled operators to verbally warn people who are littering or otherwise misbehaving. With the power of applications such as Google maps, people are starting to realize how valuable information is. At the same time, technology such as TIVO and internet is starting to allow them to protect themselves against advertisements offset by companies trying to gather more and more information about their target markets in order to re-penetrate them. | |||
</p> | |||
<p> | |||
In 2010 something happens to offset the delicate balance that has been maintained until then. A smart extremist gets his hands on private information related to powerful American politicians which allows him to blackmail them in an attempt to push his own agenda. When this comes to light the American fear of terrorism is fueled to new heights, while simultaneously making the rest of the world aware how important it is to protect private information. This happened in the same year that the EU constitution was rejected again by it’s citizens who still did not trust their politicians. | |||
</p> | |||
<p> | |||
This had several results:<br /> | |||
* In other to protect themselves, and by demand of their citizens, individual countries start creating privacy laws, which severely limits the rights for governments and corporations to gather, share and store private information | |||
* Also laws are created making institutions responsible for the data they contain and any security breaches, forcing them to give a much higher priority to making sure all the data is secure | |||
* The US alienates itself more from the rest of the world by increasing it’s border security in order to prevent more terrorist threats and reacting aggressive against Arabic countries whom they hold responsible. | |||
* China announces it will keep censoring information from the rest of the world in order to protect it’s citizens. | |||
</p> | |||
<p> | |||
In the following years these measures help shape the world. Because of the privacy laws, encryption is tuned to perfection and becomes a commodity on every communication channel. With the introduction of 5th generation mobile internet ubiquitous computing finally becomes as mainstream as mobile telephony is now. Because of this people can carry their private information always with them on their mobile computer and authorize requesters access to information, making access to private information an on demand process enforced by the laws limiting the ability for third parties to store private information. | |||
</p> | |||
<p> | |||
In 2013, this growing sense of having to be in control of your own business and not trusting others, has not helped the global political climate to recover from the 2010 events. The EU keeps struggling and actually rejects Turkey from joining, setting a precedence and making it almost impossible to accept other new members, especially Islamic countries. The US also starts to focus it’s attention to countries who threaten their laws and economy, for instance by allowing data havens, software piracy or online gambling. This forces third world countries to feel even more threatened, and continue their quest against the evil US force. | |||
</p> | |||
<p> | |||
With this information it’s not hard to guess how our world will finally look like in 2015. Peoples desire to feel safe has created a climate of having to be in control and not trusting your neighbor. Private information is protected and will only be shared when on demand and when deemed necessary. Global cooperation is at a minimum, with countries focusing on protecting their own interests. A side effect of this is that a lot of money is spent on protection, and overhead costs for international business have increased considerably resulting in slow growing economies, again putting people in a position to distrust their politicians. A safer and better world for everyone!<br /><br />... or is it ? | |||
</p> | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Presentation Movies</h1> | |||
<div style="text-align: justify; padding-bottom: 10px;">During the presentation of the scenarios above on thursday april 5th 2007, movies were used to illustrate the scenarios:<br />[http://www.bisterbosch.com/iib/scenario1.wmv Scenario 1 movie (WMV @ 20MB)]<br />[http://www.bisterbosch.com/iib/scenario2.wmv Scenario 2 movie (WMV @ 20MB)]<br />[http://www.bisterbosch.com/iib/scenario3.wmv Scenario 3 movie (WMV @ 35MB)]<br />[http://www.dplace.nl/scenario4.rar Scenario 4 movie (PPT @ 1.8MB)]<br /> | |||
</div> | |||
<h1 style="background:#e0ecf1; border-left:1px solid #AAAAAA;border-top:1px solid #AAAAAA;border-right:1px solid #AAAAAA; padding-left: 10px;">Critical Discussion</h1> | |||
While putting together the driving forces, and merging them into a systems diagram, we came to a few revelations which in hindsight might have been quite obvious.<br /> | |||
Privacy is one of the most controversial issues known to man. It is grounded in almost every ethical dilemma that man faces on a daily basis. Human rights, fairness, objectivity, violation of personal rights... All these play a role in privacy and each has to be kept in mind while piecing together plausible scenarios for the future.<br /> | |||
The problem? As we constructed the systems diagram, one thing became brutally clear and led to much delay and confusion, the fact that everything loops. Everything falls back on something else. The trick was to go up level by level, until we managed to iteratively reach a level in which we could no longer create a loop. <br /> | |||
We chose to narrow our 'axes' down to two concepts, government control and global cooperation. The level of government control and global cooperation influence the way information is held, laws about information, use of information, perception of different view, human values, and how globalization (assumed to be seemingly inevitable) influences privacy. | |||
Originally the Y-axis for our scenarios was ‘level of privacy’, however we were unaware that this was considered a tautology with our topic, which was the future of privacy. To maintain the integrity of our scenarios, we chose ‘level of government control’ as the new Y-axis. A government who wants to have a high level of control over its citizens, cannot achieve this without greatly sacrificing the privacy of its citizens. And vice versa, to guarantee the privacy of its citizens the government has to relinquish control. | |||
<br /> | |||
<!-- | |||
<hr /> | <hr /> | ||
<pagerating from="Bad" to="Good" category="Scenario">Rate this page</pagerating> | <pagerating from="Bad" to="Good" category="Scenario">Rate this page</pagerating> --> | ||
<pagerating from="Poor" to="Good" category="Scenario"> Rate this page</pagerating> | |||
Latest revision as of 15:19, 3 May 2007
Introduction
Feedback
After we presented the scenarios below, we received the following feedback.
- name the scenarios
- tautology if you have an axes describe the topic
potential axes could be the idea of distributed system of identity, vs. centralised system of identity
- work in a dominance to a certain set of technologies, rather than making it total
- remove the earning more and working less, not plausible
- address actual amount of data
- what about interconnected data
- what is the rule of law in these scenarios
Research & Information
- Questions regarding the Future of Privacy
- Sources of information and interesting links
- GOOGLE VIDEO: The Power of Nightmares 3 of 3 - In this eye-opening video, a more realistic view is given of terrorism, and the 'War Against Terror'
Driving Forces
Driving forces categorized by PEST factors method.
Every driving force in the categories below are built up out of predetermined constituents: Description, Enablers, Inhibitors, Paradigms, Experts, Timing, and Web Resources
Political
New
- Perception_of_Terror - The perception of terror is slowly changing
- immigration - Growing immigration in the western countries
- European_Union - Growing European Union
- cybercrime - Upcoming internet criminality (cybercrime)
Existing
- War on terror - War on terror
- Terrorism - Terrorism
- Global Terrorism - Global Terrorism
- Control of the Internet - Control over the internet
Economic
New
- Electrical component costs - Cheaper integration of cameras or audio-recording equipment
- Disclosure for tax purposes - Information disclosure
- Exchange rates - Cheaper wholesale of electrical components, leading to cheaper integration
- Purchasing power - A country with high purchasing power can spend more on invading or preventing physical invasion of privacy
Existing
Social
New
- Globalization - improvement on existing Driving Force
- Curiosity to cultural differences
- Increasing individualization
- Increasing Demand for new types of entertainment
Existing
- Mobility
- Increasing social isolation
- The Globalization of Culture (or Cultural Globalization)
- Community Feeling
- Chinese people's increasing leisure time
- Movement Towards World Unification
- Urbanization and Social Status
Technological
New
Existing
- Virtual Communities
- GPS Evolution
- Increasing Use of e-Commerce
- The Increasing Use of Internet
- Reduction of organizational and technological complexity
- The war on Spy- and Ad ware
- Whereabout the fourth generation mobile technology
Diagrams
Systems diagram
Version 1 - 'Brainstorm' edition
In order to start creating a system diagram, the initial, unmodified driving forces were mapped into a 'brainstorm' system diagram.
This version seemed to revolve around two concepts; Globalization and Terror(ism). Feedback provided lead to the conclusion that:
A) Globalization should be split up into more defined driving forces
B) Globalization and terrorism are on their own very complex topics at this moment, so they require further in-depth research.
C) Politic, as found as a driving force, is a category. An actual driving force must be specified from this category.
Terrorism is something most people associative with the rhetoric as presented by the media, however, there is a difference between the reality and the rhetoric. Our task is to find our the difference so we can correctly find some distilled driving forces.
This version will be improved upon once the extra research has been completed and posted as version 2 below.
Version 2 - Completing
This is the second version of out system diagram. The two centered spots we had in the first diagram are now worked out. We changed 'terror' in 'perception of terror' and 'Globalization' is worked out in several new parts. A lot of aspects still missing though.
Planning for version 3:
- Clear inhibitor/enabler distinction
- Improved edge naming
- More driving forces
- Logic fixes
Version 3 - Semi-Final
This is the semi-final version of the systems diagram. Messy, but complete. However there is always room for more loops and additions, but through feedback loops and other control mechanisms we managed to keep it to a minimum.
Defining the scenarios
To define our scenarios we used an experimental technique. We created two possible futures during a clay dough session in which scenarios were visualized. The first possible future concerned future events relating to the driving forces that each group member had worked on. For the second future every group member pictured a news paper article in the future concerning privacy on a slow newsday.
With these two futures we were able to find some common denominators for all events that were depicted. Each event contained a level of global cooperation and a certain level of government control. This is how we established the X and Y-axis that we used for our scenarios. In the picture on the left all the events are placed within these axis. These events are not necessarily used in the scenarios, but merely functioned as guidelines to establish the main drivers of our actual scenarios.
Scenarios
Scenario Axes
Scenario 1: Closeness from seclusion
In 2015, everybody is aware of their own status of privacy, and in full control of it. Laws are in place to protect personal information, allowing information only to be used for the exact purposes it was given out for by the owner. Technology has made it possible to transmit and store information in utter privacy, while new-age complex encryption technologies make this possible. People carry their private information with them in transmittable format at all times. Back in 2007 this was already a non-issue seeing as personal portable data storage devices the size of cigarette lighters and smaller already had a capacity of up to four gigabyte. This amount is more than sufficient to store any person-critical information of any format. Also, physical privacy is improved with devices to scramble electronic signals, being able to create Faraday-like cages around personal areas, this was still a problem in 2007 as there was no such thing as a 100% secure personal storage device.
People feel safer as they know exactly what is known of them by whom, when and where.
Laws are in place to protect people’s privacy unconditionally, also when moving around, which makes migration between different countries a political nightmare, but due to high global cooperation, this problem was solved as governments worked together to agree on wide-spread privacy laws. However, this poses a problem for the rule of law concerning the storage and use of private information. Giving the people the power over their own information reduces the control a government has over the information. The government can then no longer decide how to use the information. The question is then whether there should be special laws excluding certain occasions, controlled by the government, in which the privacy of the people can be abused.
Around 2005, personalized advertising was thought to be the future. However, with the new privacy laws and people being critical of who gets access to their data, there is no room for personalized advertising. Advertising stagnates. Since technology has made it near impossible to create online advertising, it is a marketing-man’s nightmare. Economic recession follows shortly for a brief period of time as retailers recover and fall back to more primitive methods of marketing. The vast growing network of virtual communities is inhibited as no data is communicated and the communities are very impersonal. People are weary of spreading their personal data and hold onto it very well, leading to social interruption, individualization and isolation.
As data is not kept, or may not be kept without permission, bureaucratic practices are rising. Constantly having to ask permission for everything and from multiple people increases the amount of communication needed per transaction. Thankfully, technological advancements in communication compensate for this reasonably well. The crucial data per person, perhaps including electronically stored biometrics and photographs, does not, and seemingly, will not exceed the exorbitant amount of 512 megabytes. Of this amount, only some of it is relevant to be copied at designated places. At an airport, they might only be interested in one or two pictures, your social security number, name, height, age, and a few others figures. This would total a much smaller amount than the total stored. Transferring approximately 50 megabytes takes less than a quarter of a second. This poses no problem for mass reading of multiple data from multiple people uses multiple media (wireless, wired, scanners).
Perception of terror has been limited to more reality and less speculation and media-induced ideology. The hype has been suppressed. How could anybody possible still attack me? They don't know anything about me!
I love how we've gotten so close.....what's your name again?
Scenario 2: Global Privacy
The year is 2015. As the world was changing fast for the last couple years, privacy eroded slowly. Governments are connecting throughout the entire world, not only the EU is rapidly growing, also there are incentives to connect the EU to the US. Cultures came together and cultural differences slowly changed and overlapped which leaded to individualism. The amount of immigration was slowly taken back just because of the globalization and uniting countries. Extremism and crime was slowly taken down by the integration. People got very happy as they were feeling very safe in a world with less terror and crime.
New technologies came available which made everyone and everything traceable. The amount of privacy was therefore lowering but almost nobody was caring as long as they were safer. All the uniting countries agreed on one global data warehouse and a world identity. Due to this traceability almost all (cyber)crimes were solved and SPAM was not possible anymore. The use of internet got a more important role in the world society. Everyone has a virtual identity which is not only used for playing games but also virtual businesses are rapidly growing. Internet made it possible to store exchanged information. Phone calls were only made via VOIP. Other technological evolutions were used to integrate people among various ‘countries’. Digitalizing the world took care of disappearing brick and mortar shops. The internet was now the way to do your shopping and as it evolved the amount of literacy found in a ‘normal’ book format was brought back to only a few. The digital literacy period has been entered where every information and book you wanted to read was for free available. All these information could more easily be found as you credentials and information searches were profiled on the internet with public access by companies.
The political power was equally divided, which got some resistance from the largest former countries in the world. The world got into economic recession but was slowly recovering as the politicians agreed on changing laws and making things more globally.
Scenario 3: Forwards to explosion
This 3rd scenario is based on the future with high government control, which leads to low level of privacy in the world where global cooperation wasn’t really developing and stayed in almost the same level as it is now.
Today with growing economy level in so called “developing” countries the amount of emigrates will slowly decrease. This will lead to several changes in different sectors. First of all, with increase of living standards, people will be more able to use communication technologies and media. The result will be huge invasion into personal privacy. Interruption of privacy at that moment will be not only because people are able to do that, and they are curious in others personal life, but also because of today politics there will be intervention. In other words there is a growing protection from terrorism: so called “world protectors” and “anti-terrorists” are searching all over the world the dangerous information. This is done without yours personal permission and there is nowadays almost no protection for that. Besides that, the new safety video cameras are working with the same idea: intervention into yours privacy without yours admission to protect from possible damage or danger. Additionally, politics very often not only misinterpret but also misuse information. To conclude, privacy invasion is grown to a new level: from leisure to protection from possible danger.
The other point necessary to mention is, that people nowadays don’t really care how much and how personal/ important information they put for example on the internet. As mentioned before, politics often misuse the information, but there are many other segments where unsafe information could be used. Of course, the information can be used not only for damaging, but some people can gain advantage of it, like personalized advertisement or helping with tax filling (for example DigiD in the Netherlands).
With growing software and hardware and other many technologies the level of protection will be not enough to secure it. Constant hacks into sensitive databases will lead to decrease of retained information. Of course with possible transparency the level of interventions could decrease, and everybody in “illegal” privacy activities will be caught. Unfortunately the cyber-crime (phishing, hacking, scripting, malicious code and spamming) is still growing. The data can be 99% secure, but the possible brake into especially important information can cause really big damages.
Adding to this point, people, who are willing to save time on online activities: web-shopping, banking, phoning, etc. need to give up a lot of necessary (or not) personal data. This leads to riot of privacy issues: people who are involved directly and understand the importance of shared information aren’t willing to distribute it. Within this scenario they will suffer the most. Others are not interested yet, but they will get the grunt of privacy issues too. This should lead to new laws for protection of privacy, but the basic damage is already done.
To conclude, within this scenario, in around 2015 while regular people will have advantages, unfortunatelly they will suffer the most. Thought the criminals (probably politics too) will have huge advantages of it.
Scenario 4: Save yourself!
When looking at the world now, you might be optimistic about future cooperation, but actually the signs undermining this vision are already sounding their warning bells very loud and clearly. The efforts by the WTO to open up trade borders are actually seen by 3rd world countries as a way of economic colonization. This has for instance triggered Bolivia, Cuba and Venezuela to form an ‘axis of good’ to oppose the capitalist US which they see as an ‘axis of evil’. Cuba under leadership of Evo Morales has also nationalized the natural gas industry, turning the wheel on open markets backwards. This economic rift between the first world and the third world is also visible in the military interventions and ‘peace keeping’ missions send out by first world countries. Also between the rich countries there is more friction then one might suspect, with the US pushing to invade privacy more in order to prevent terrorist attacks and even forcing instances in Europe to give up data which should be protected by European privacy laws. Going even a step further Bush has signed a law that authorizes the use of military force to liberate any American or citizen of a U.S.-allied country being held by the [International Criminal] court, which is located in The Hague.
All this anonymity combined with a growing awareness that governments and private institutions might know too much about the people helps to fuel a feeling of distrust and of not being safe. Some governments like the UK try to fight this by invading it’s civilians privacy even more, for instance, their latest effort was to install talking security camera’s, which enabled operators to verbally warn people who are littering or otherwise misbehaving. With the power of applications such as Google maps, people are starting to realize how valuable information is. At the same time, technology such as TIVO and internet is starting to allow them to protect themselves against advertisements offset by companies trying to gather more and more information about their target markets in order to re-penetrate them.
In 2010 something happens to offset the delicate balance that has been maintained until then. A smart extremist gets his hands on private information related to powerful American politicians which allows him to blackmail them in an attempt to push his own agenda. When this comes to light the American fear of terrorism is fueled to new heights, while simultaneously making the rest of the world aware how important it is to protect private information. This happened in the same year that the EU constitution was rejected again by it’s citizens who still did not trust their politicians.
This had several results:
- In other to protect themselves, and by demand of their citizens, individual countries start creating privacy laws, which severely limits the rights for governments and corporations to gather, share and store private information
- Also laws are created making institutions responsible for the data they contain and any security breaches, forcing them to give a much higher priority to making sure all the data is secure
- The US alienates itself more from the rest of the world by increasing it’s border security in order to prevent more terrorist threats and reacting aggressive against Arabic countries whom they hold responsible.
- China announces it will keep censoring information from the rest of the world in order to protect it’s citizens.
In the following years these measures help shape the world. Because of the privacy laws, encryption is tuned to perfection and becomes a commodity on every communication channel. With the introduction of 5th generation mobile internet ubiquitous computing finally becomes as mainstream as mobile telephony is now. Because of this people can carry their private information always with them on their mobile computer and authorize requesters access to information, making access to private information an on demand process enforced by the laws limiting the ability for third parties to store private information.
In 2013, this growing sense of having to be in control of your own business and not trusting others, has not helped the global political climate to recover from the 2010 events. The EU keeps struggling and actually rejects Turkey from joining, setting a precedence and making it almost impossible to accept other new members, especially Islamic countries. The US also starts to focus it’s attention to countries who threaten their laws and economy, for instance by allowing data havens, software piracy or online gambling. This forces third world countries to feel even more threatened, and continue their quest against the evil US force.
With this information it’s not hard to guess how our world will finally look like in 2015. Peoples desire to feel safe has created a climate of having to be in control and not trusting your neighbor. Private information is protected and will only be shared when on demand and when deemed necessary. Global cooperation is at a minimum, with countries focusing on protecting their own interests. A side effect of this is that a lot of money is spent on protection, and overhead costs for international business have increased considerably resulting in slow growing economies, again putting people in a position to distrust their politicians. A safer and better world for everyone!
... or is it ?
Presentation Movies
Scenario 1 movie (WMV @ 20MB)
Scenario 2 movie (WMV @ 20MB)
Scenario 3 movie (WMV @ 35MB)
Scenario 4 movie (PPT @ 1.8MB)
Critical Discussion
While putting together the driving forces, and merging them into a systems diagram, we came to a few revelations which in hindsight might have been quite obvious.
Privacy is one of the most controversial issues known to man. It is grounded in almost every ethical dilemma that man faces on a daily basis. Human rights, fairness, objectivity, violation of personal rights... All these play a role in privacy and each has to be kept in mind while piecing together plausible scenarios for the future.
The problem? As we constructed the systems diagram, one thing became brutally clear and led to much delay and confusion, the fact that everything loops. Everything falls back on something else. The trick was to go up level by level, until we managed to iteratively reach a level in which we could no longer create a loop.
We chose to narrow our 'axes' down to two concepts, government control and global cooperation. The level of government control and global cooperation influence the way information is held, laws about information, use of information, perception of different view, human values, and how globalization (assumed to be seemingly inevitable) influences privacy.
Originally the Y-axis for our scenarios was ‘level of privacy’, however we were unaware that this was considered a tautology with our topic, which was the future of privacy. To maintain the integrity of our scenarios, we chose ‘level of government control’ as the new Y-axis. A government who wants to have a high level of control over its citizens, cannot achieve this without greatly sacrificing the privacy of its citizens. And vice versa, to guarantee the privacy of its citizens the government has to relinquish control.
<pagerating from="Poor" to="Good" category="Scenario"> Rate this page</pagerating>