Difference between revisions of "Security Technology"
| Line 13: | Line 13: | ||
==Enablers:== | ==Enablers:== | ||
Internet technology | Internet technology <br> | ||
Leak cases | Leak cases<br> | ||
Privacy policy | Privacy policy<br> | ||
Digital advertising technology | Digital advertising technology<br> | ||
Revision as of 20:37, 17 September 2009
Description:
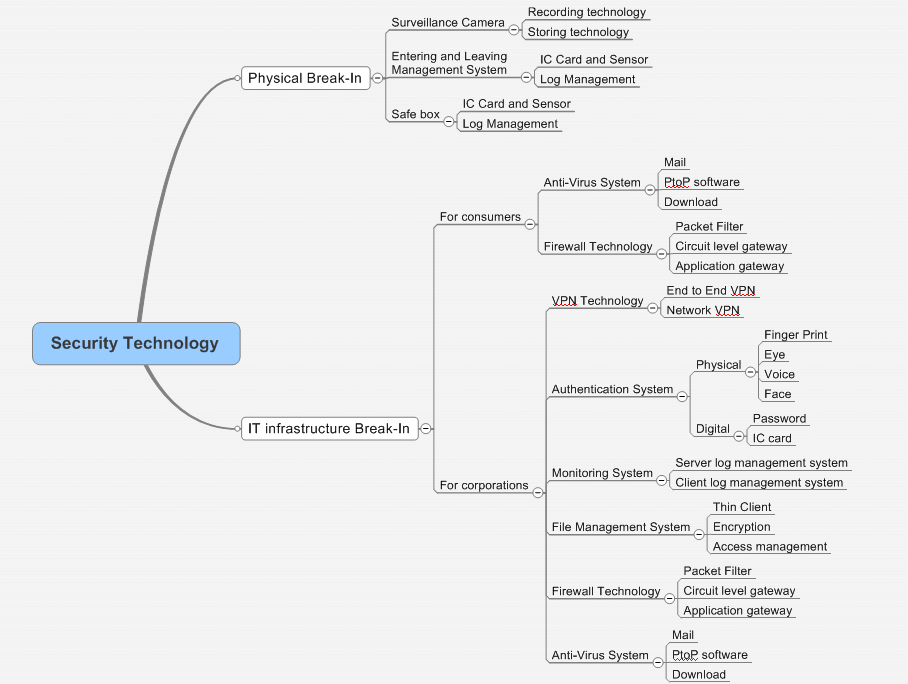
Numerous leak cases through both physical and IT infrastructures have been making consumers and corporations reluctant to give out their privacy information for digital advertisements. The prevalence of security technology can be a key to mitigate the trend and prosper the digital advertisement. Security technology can be categorized into the one against physical break-in and the one against IT infrastructure break-in.
<Physical Break-In> Privacy information can be leaked through physical break-ins. Safety box, surveillance camera and entering and leaving management technologies contribute to protecting from such leakage. According to the research from Secom, 80% of the leak cases attribute to the internal leakage, that is, the leakage caused by people who owned or were authorized to access the information. Thus, besides recording the activities, solid log management would be significantly required.
<IT infrastructure Break-In>
Varied solutions both for consumers and corporations have been developed in this segment. Nowadays, anti-Virus technologies are essential to protect personal information. Viruses which analyze and send out the privacy stored in PC hard drive are often attached in email and downloaded files from web sites. Moreover, P to P software installed in private PCs such as Winny has caused numerous leak cases for confidential information including customer databases. Firewall is necessary to prevent intrudes from other computers. Corporations are required higher level of approach shown in the diagram.
Enablers:
Internet technology
Leak cases
Privacy policy
Digital advertising technology