Difference between revisions of "Security Policy"
| Line 17: | Line 17: | ||
==Paradigms:== | ==Paradigms:== | ||
Strict security regulations convince corporations that they now have an additional area to invest in order to maintain their corporate activities. Consolidation of the security system used to be a corporate strategy that leads to an enhancement of the brand image, but it has become a commitment without which corporations cannot survive. The regulations also mitigate fear of the consumers who are reluctant to utilize the internet technology, consequently stimulating digital advertisement business. | |||
==Experts:== | ==Experts:== | ||
==Web Source:== | ==Web Source:== | ||
Revision as of 20:52, 17 September 2009
Description:
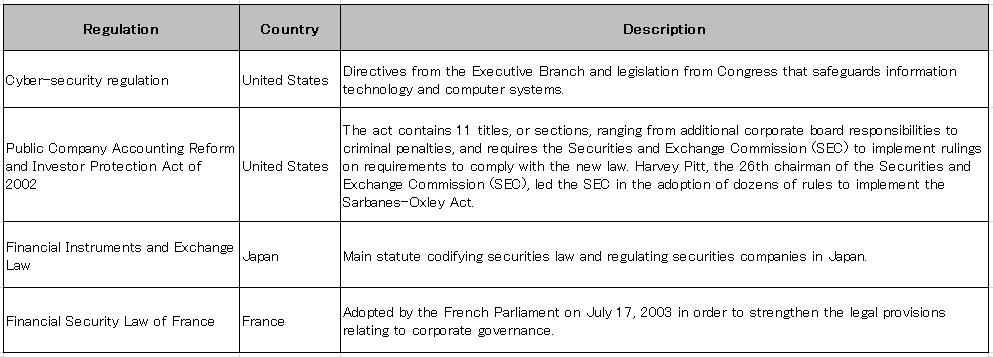
Undeveloped policy regarding personal information contributed to an enhancement in consumers’ sensitivity to the privacy. Against a back drop of some serious leak cases, governments established security regulations for corporations to protect their citizens from security risks. The table below shows the regulations that have been enacted in recent years. Following the Sarbanes-Oxley Act established in the United States, varied countries including Japan, Germany and France have developed the laws regarding security especially for cyber attacks. Such regulations have been inducing the development and prevalence of security technologies.
The United States government believes the security of computer systems is important to the world for two reasons. The increased role of Information Technology (IT) and the growth of the e-commerce sector, have made cyber-security essential to the economy. Also, cyber-security is vital to the operation of safety critical systems, such as emergency response, and to the protection of infrastructure systems, such as the national power grid. Cyber-security measures include firewalls, anti-virus software, intrusion detection and prevention systems, encryption and login passwords. Federal and state governments in the United States have attempted to improve cyber-security through regulation and collaborative efforts between government and the private-sector to encourage voluntary improvements to cyber-security.
The Internal Control Committee of the Business Accounting Council of the Japanese Financial Services Agency provided final Implementation Guidance for Management Assessment and Audit of Internal Controls over Financial Reporting (ICFR) in February 2007. The Implementation Guidance provides details to Japanese companies on how to implement a Management Assessment of Internal Control over Financial Reporting as required under the Financial Instruments and Exchange Law.
Similar to the American Sarbanes-Oxley Act, the Financial Security Law of France rests mainly on an increased responsibility of leaders, a strengthening of internal control and a reduction in the sources of conflicts of interest.
Enablers:
Leak cases
Inhibitors:
Excess financial damage to corporations due to a cost increase
Paradigms:
Strict security regulations convince corporations that they now have an additional area to invest in order to maintain their corporate activities. Consolidation of the security system used to be a corporate strategy that leads to an enhancement of the brand image, but it has become a commitment without which corporations cannot survive. The regulations also mitigate fear of the consumers who are reluctant to utilize the internet technology, consequently stimulating digital advertisement business.