Difference between revisions of "Scenario 1: bottom-up Internet"
| Line 10: | Line 10: | ||
Large information and service providers like Google, Amazon/Yahoo and Microsoft collect more and more data from the consumers which they couple together to offer customized solutions. | Large information and service providers like Google, Amazon/Yahoo and Microsoft collect more and more data from the consumers which they couple together to offer customized solutions. | ||
==2008 The Giants gain ground== | ==2008/2009 The Giants gain ground== | ||
More and more applications get ported to web based applications where unlimited online storage of the documents on mirrored servers makes sure that no documents are ever lost because of computer crashes. | More and more applications get ported to web based applications where unlimited online storage of the documents on mirrored servers makes sure that no documents are ever lost because of computer crashes. This is all possible because of the advances in hardware development, the introduction of Holographic storage has really taken off and 2 terabyte disks and 240 terabyte storage boxes are ordered in large quantities. | ||
More and more users are attracted by the increased user friendliness and the battle between the service provider giants rages on and the increased user friendliness in those services causes more and more information to be coupled and stored together. | |||
Several studies are started to determine the amount of shared data and the influences on safety and privacy of the users. | Several studies are started to determine the amount of shared data and the influences on safety and privacy of the users. | ||
==2009 The year of no secrets== | ==2009 The year of no secrets== | ||
Revision as of 11:32, 14 May 2006
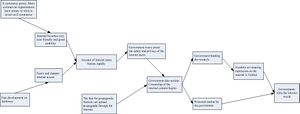
Big Brother pulling the strings
In this scenario on the future about the bottom-up Internet the goverments worldwide will take control, timeline by Andrew, scenario by Jim
2006/2007 The web keeps on growing
During the next two years the internet keeps spreading to all parts of the world. The open source sector itself gets a boost because of the increase in “poor” users that are willing to contribute to pay less. Web applications take off and remain as user friendly as possible because of the joint growth of the Bottom up user solutions and the top down corporation solutions.
Several advances are made in hardware and software areas causing the average browsing speed to tenfold. This in turns fuels the possibility to offer more (bandwidth intense) products.
Large information and service providers like Google, Amazon/Yahoo and Microsoft collect more and more data from the consumers which they couple together to offer customized solutions.
2008/2009 The Giants gain ground
More and more applications get ported to web based applications where unlimited online storage of the documents on mirrored servers makes sure that no documents are ever lost because of computer crashes. This is all possible because of the advances in hardware development, the introduction of Holographic storage has really taken off and 2 terabyte disks and 240 terabyte storage boxes are ordered in large quantities.
More and more users are attracted by the increased user friendliness and the battle between the service provider giants rages on and the increased user friendliness in those services causes more and more information to be coupled and stored together.
Several studies are started to determine the amount of shared data and the influences on safety and privacy of the users.
2009 The year of no secrets
Because of several Bottom Up projects failing a lot of developers become disgruntled and focus there attention on proving the un-safety of storing so much information together. This means hacking and publicising all kinds of data stored by the giants.
The initial results of the studies performed support the un-safety and possibilities for miss-usage of data. A lot of internet users feel threatened and start protesting and suing the giants. Most outcomes of these cases state that the giants handled according to the law and that they are not to be held responsible.
2010
Governments acknowledge the results of the studies and create new laws for data storage and combination, causing the giants to rethink their strategy. Also government studies are started to research if it would be possible to manage/store the data themselves some actually have hidden agendas here and want information control.
2011
Several governments use the fear of lost privacy to implement information storage systems that are the only allowed systems to store personal data in large quantities. Some of these even go further and start censoring certain information argument as “privacy” sensible.
At the end of this year people become aware of this and start protesting. This influences the bottom up internet to grow to go around these regulations.
201x
In the end everything finds a new balance